Log in with ZITADEL on Gitlab OmniAuth Provider
This guide shows how to enable login with ZITADEL on self-hosted Gitlab instances.
It covers how to:
- create and configure the application in your ZITADEL project
- create and configure the connection in a self-hosted Gitlab instance
Prerequisites:
- existing ZITADEL Instance, if not present follow this guide
- existing ZITADEL Organization, if not present follow this guide
- existing ZITADEL project, if not present follow the first 3 steps here
- running Gitlab instance see installation guide
Create the Gitlab app
Go to the detail page of your project and click the "+"-button in the application-section. This will lead you to the the creation wizard.

Create the app by setting a name and select the application type "Web"
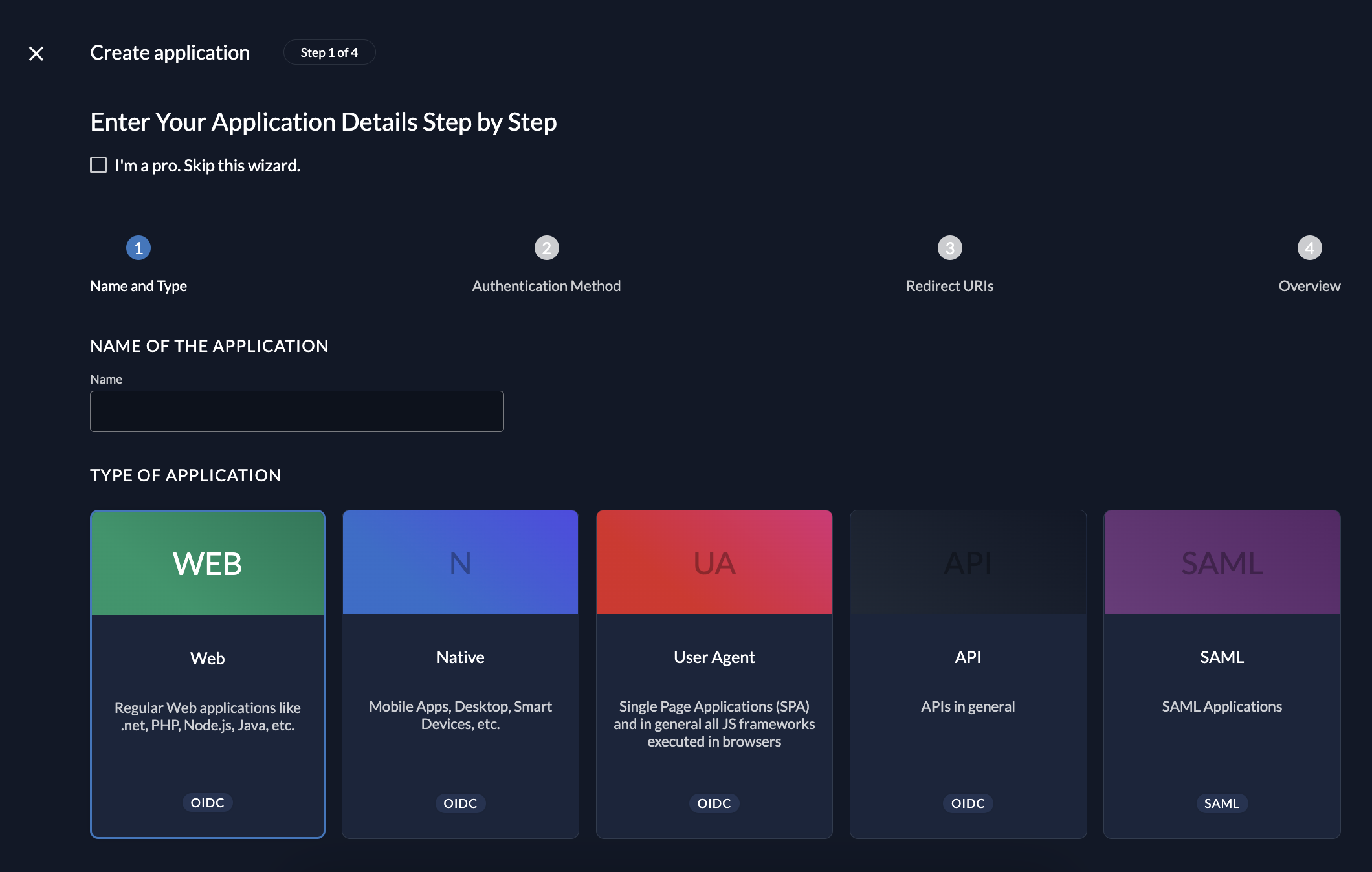
Select the authentication method
The authentication method defines the communication flow during a login
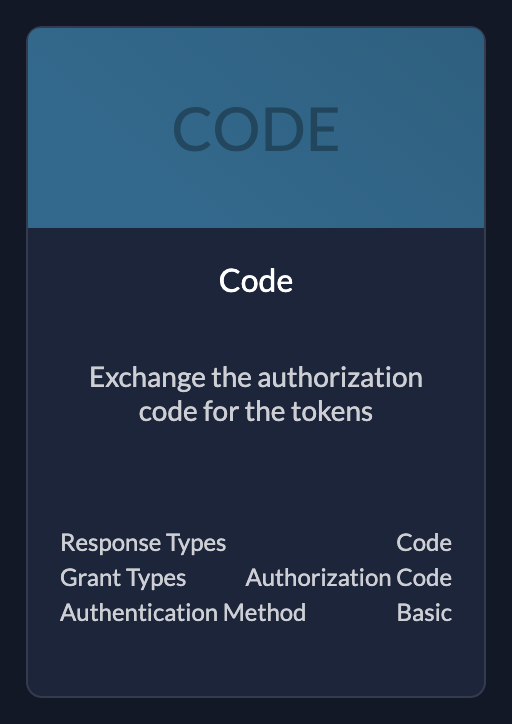 | CodeUse if your application needs client id and client secret |
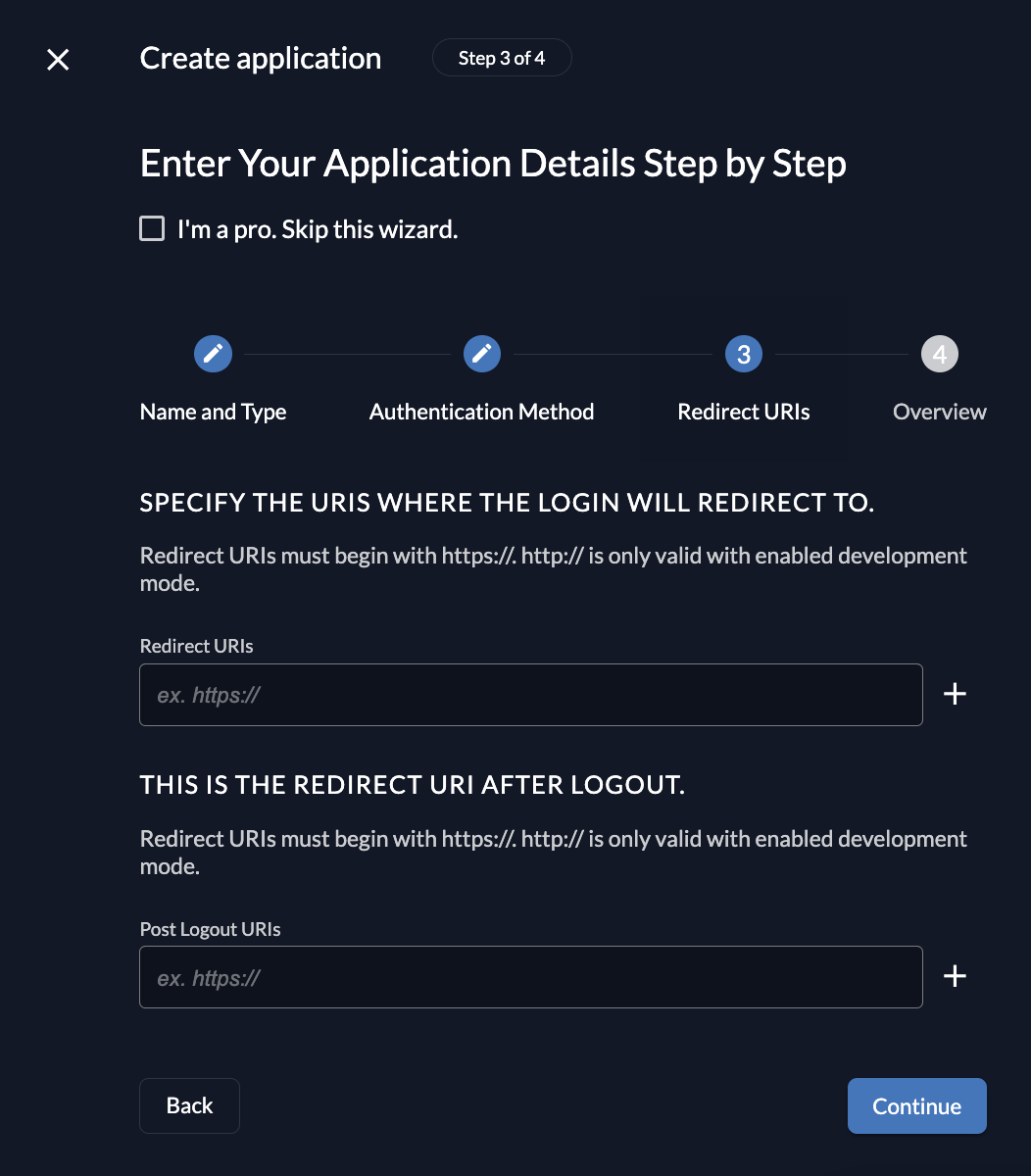
Redirect URIs
During the login flow the application defines where a user is redirected to after login or logout.
ZITADEL verifies if the URL the user gets redirected to is valid by checking if one of the redirect URIs match.
- Redirect URIs are verified during the login process.
- The default redirect uri of your app is
https://<your_gitlab_url>/users/auth/openid_connect/callback - Post Logout URIs are verified during the logout process.
The default redirect uri of your app is https://<your_gitlab_url>/users/auth/openid_connect/callback
Review your configuration
The last page of the stepper shows a summary of what will be created. After you have reviewed the configuration you can create the application.
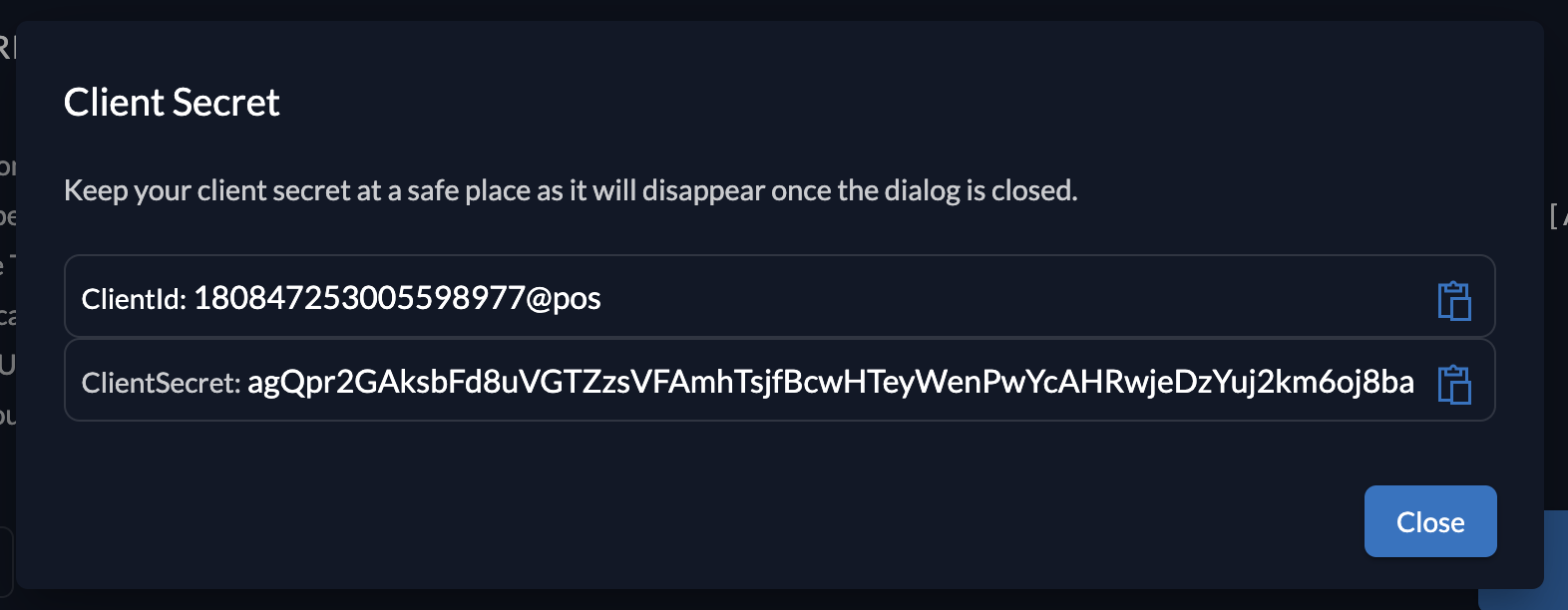
Client information
Please make sure to safe the client id and secret for later use in the application.
Gitlab configuration
Follow this guide of gitlab to configure the omniauth provider. Following is an example configuration with redacted secrets.
Replace the values of the following fields:
args.client_options.identifierwith theClientIdgenerated by ZITADEL in the last step of [Create application in ZITADEL])()args.client_options.secretwith theClientSecretgenerated by ZITADEL in the last step of [Create application in ZITADEL])()args.client_options.redirect_uriwith the proper URL to your gitlab instance and callback
gitlab_rails['omniauth_providers'] = [
{
name: "openid_connect",
label: "ZITADEL",
icon: "https://<YOUR_DOMAIN>/ui/console/assets/icons/favicon-32x32.png",
args: {
name: "openid_connect",
scope: ["openid","profile","email"],
response_type: "code",
issuer: "https://<YOUR_DOMAIN>",
discovery: true,
client_options: {
identifier: "<CLIENT ID from ZITADEL>",
secret: "<CLIENT SECRET from ZITADEL>",
redirect_uri: "https://<YOUR_GITLAB_URL>/users/auth/openid_connect/callback"
}
}
}
]